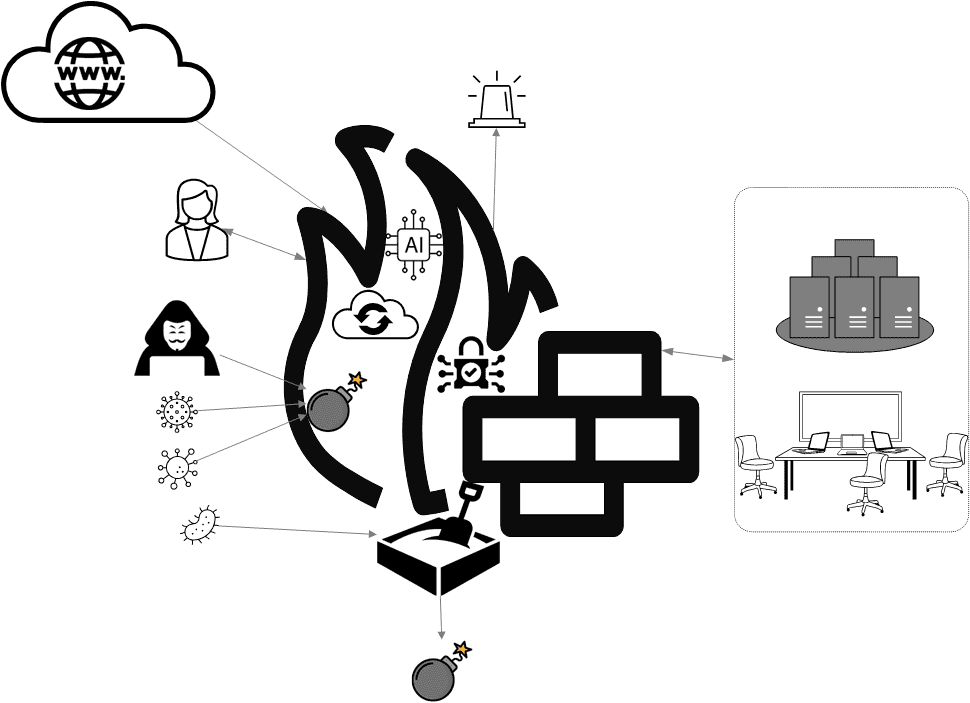
Protect Your Business from Cyber Threats
Identity and Access Management
- Implement and manage Single Sign On (SSO) solutions
- Azure Active Directory with Conditional Access for 70% of customers
- Okta Adaptive MFA and Universal Directory for MacOS, Google, and larger enterprises

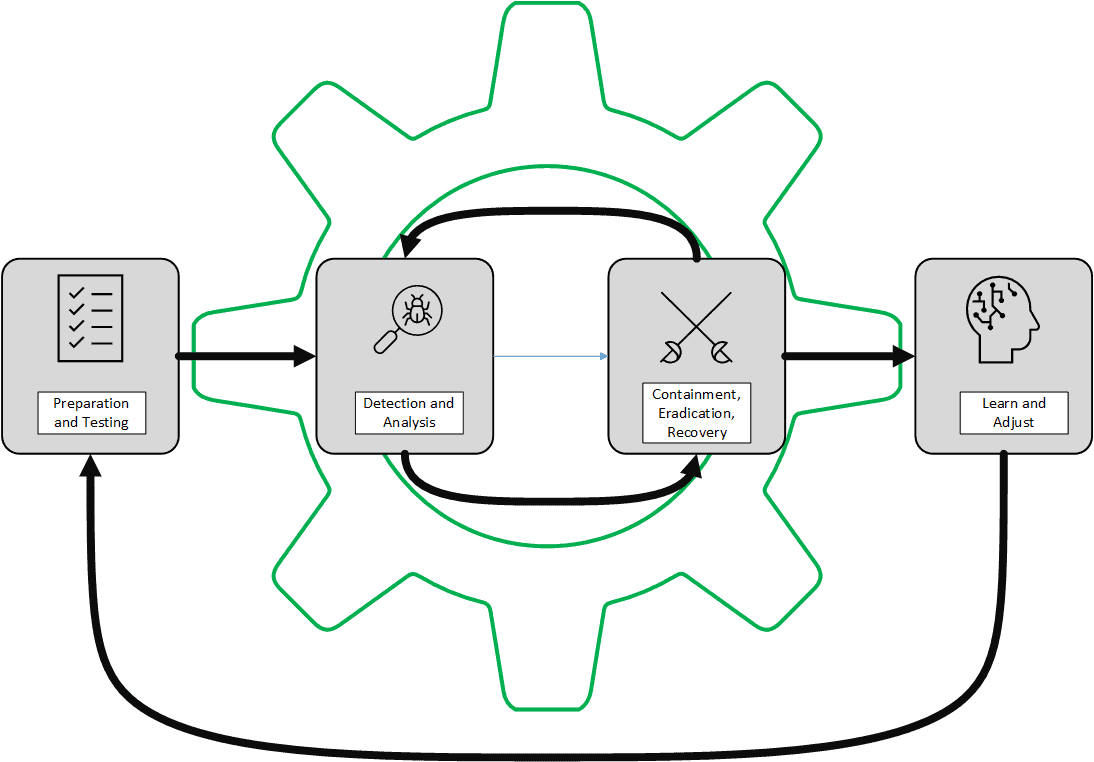
Cyber Incident Response
Preparation and Testing:
- Hire a 3rd party to regularly audit and test your controls.
- Keep business stakeholders aware of risks and mitigation strategies
- Plan communication strategy
Detection and Analysis
- 100% endpoint detection and reponse compliance
- Eliminate false positives to prevent alert fatigue
- Employ multiple malware detection systems
Containment, Elimination, and Recovery
- Assume everything is compromised
- Clean separation between corrupt and not to minimize duplication of effort
- Business continuity and productivity is always guidepost
Learn and Adopt
- It is an arms race, keep competing
- Implement controls applicable to the legal or financial requirements
- Forensics firms will provide root cause analysis to aid in rebuilding
The Basics

(Azure) Active Directory

Group Policy Hardening
Tabletop Exercises

Access Control Reviews
Security Patch Management
Endpoint Manager
Cybersecurity you can understand.
I’m so happy to have GenIX at the helm of our IT’s cybersecurity.